-

Encryption
1️⃣ Why is Encryption Important? ✅ Data Security: Protects sensitive information from hackers.✅ Privacy: Ensures only authorized users can access…
-

What is Data Hiding?
Data hiding is a cybersecurity and programming concept that restricts access to certain information to enhance security, privacy, and maintainability.…
-

What is Abstraction?
Abstraction is the concept of hiding complexity and showing only the essential details while suppressing the underlying implementation. It is…
-
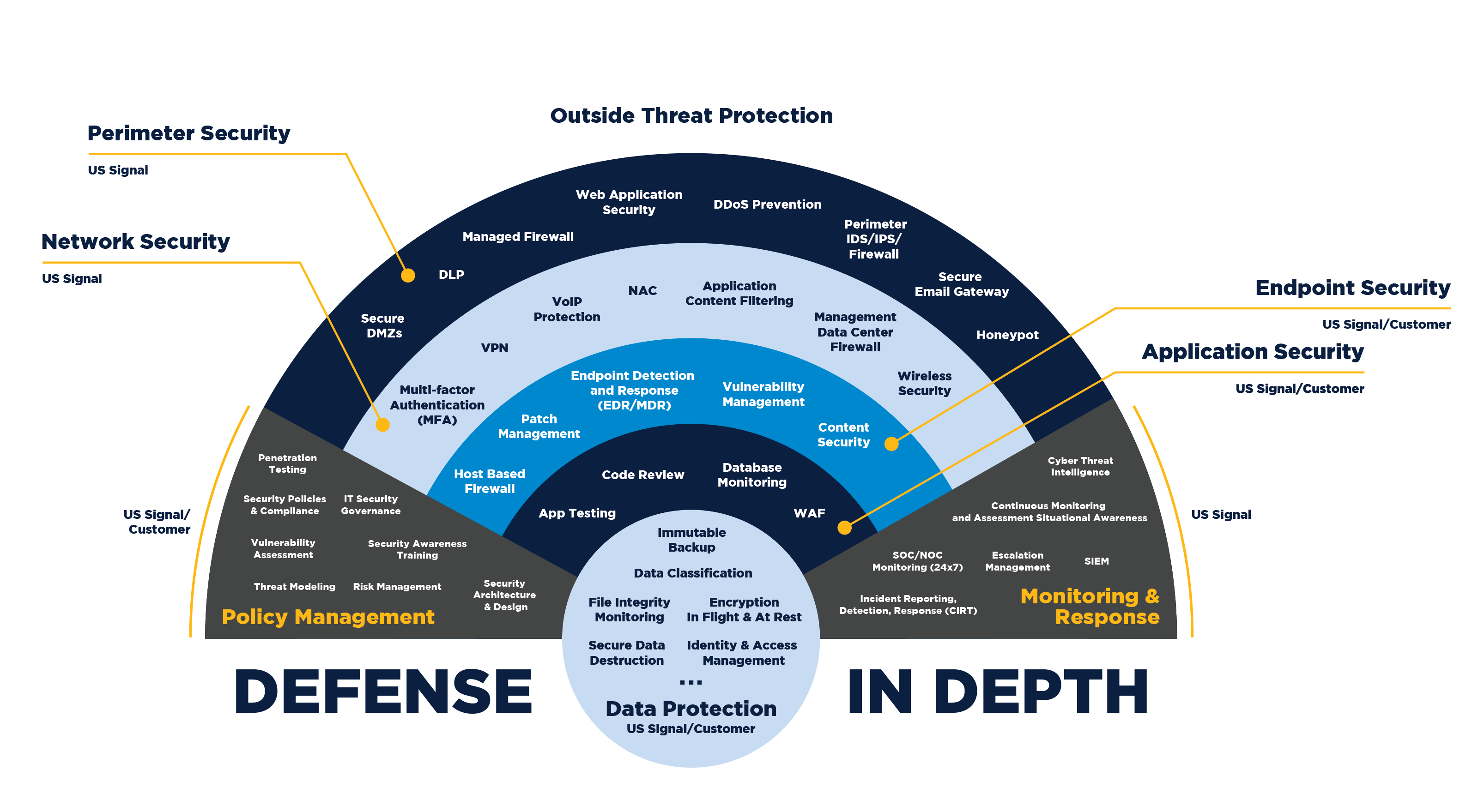
Defense in Depth (DiD)
A Multi-Layered Security Strategy Defense in Depth (DiD) is a cybersecurity strategy that implements multiple layers of security controls to…
-

Business Impact Analysis (BIA) for a Financial Company
Let’s apply the Business Impact Analysis (BIA) process to a financial company while aligning it with CISSP principles. A financial…
-

How the Delphi Technique Works in Cybersecurity
1️⃣ Expert Panel Selection – A group of cybersecurity experts is chosen based on their knowledge and experience in areas…
-
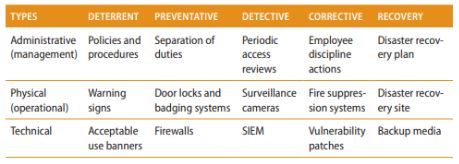
Types and Purpose of Security Controls
Security controls are measures designed to protect the confidentiality, integrity, and availability (CIA Triad) of systems and data. These controls…
-
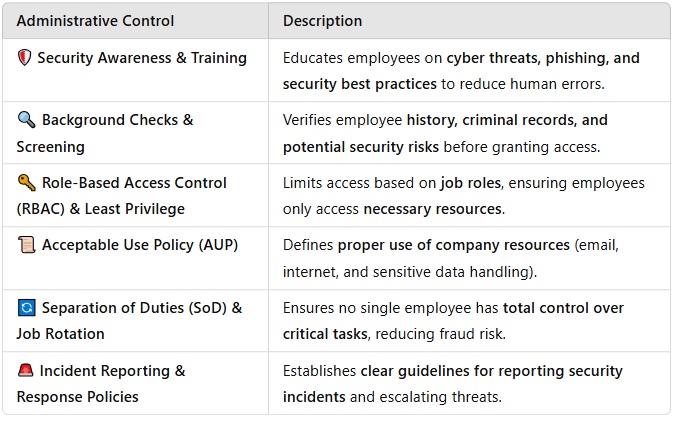
Six Administrative Controls to Secure Personnel
Administrative controls are policies, procedures, and practices designed to manage personnel security risks in cybersecurity. These controls ensure that employees…
-
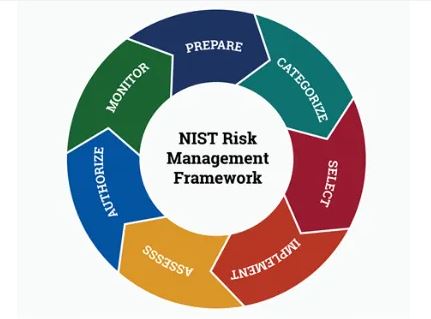
RMF (Risk Management Framework)
The Risk Management Framework (RMF) from NIST (National Institute of Standards and Technology) is a structured, seven-step process that helps…
-
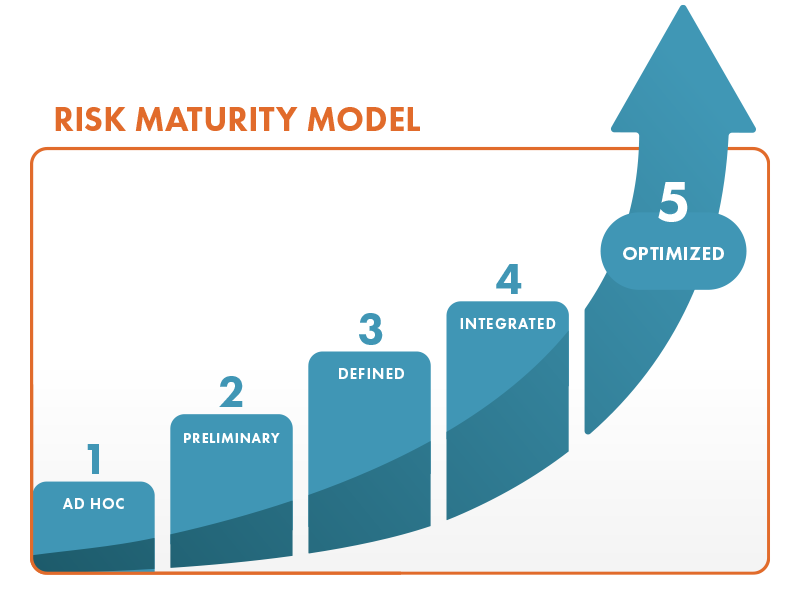
Is Your Risk Management Strategy Mature Enough?
Risk isn’t just something to react to—it’s something to manage proactively. That’s where RMM (Risk Maturity Model) comes in. It…

