A strong security policy and solution deployment require a structured approach to protect systems, data, and users. Three key security models—CIA (Confidentiality, Integrity, Availability), DAD (Disclosure, Alteration, Destruction), and AAA (Authentication, Authorization, Accounting)—play a crucial role in ensuring a resilient security framework.
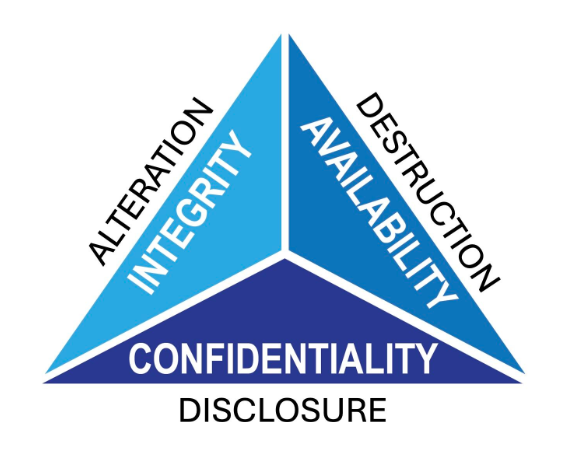
1. CIA Triad: The Foundation of Security Policies
The CIA triad defines the core security principles that guide policy creation and technology implementation:
🔹 Confidentiality
Ensuring that sensitive data is only accessible to authorized individuals.
✅ Security Policy Considerations:
- Define access control policies (e.g., role-based access control – RBAC).
- Implement least privilege and need-to-know principles.
- Establish encryption standards for data at rest and in transit.
✅ Security Solution Deployment:
- Use encryption (AES, TLS) for securing sensitive data.
- Implement multi-factor authentication (MFA) to prevent unauthorized access.
- Deploy firewalls, VPNs, and access control lists (ACLs) to restrict network exposure.
🔹 Integrity
Ensuring that data remains accurate and unaltered by unauthorized modifications.
✅ Security Policy Considerations:
- Define policies for data validation and integrity checks.
- Establish logging and monitoring requirements.
- Implement change management controls for critical systems.
✅ Security Solution Deployment:
- Use hashing (SHA-256, HMAC) for verifying data integrity.
- Deploy file integrity monitoring (FIM) and digital signatures.
- Implement version control and audit logs to track data modifications.
🔹 Availability
Ensuring that systems and data are accessible when needed.
✅ Security Policy Considerations:
- Define uptime and recovery time objectives (RTO).
- Establish redundancy and failover mechanisms.
- Implement business continuity and disaster recovery (BC/DR) plans.
✅ Security Solution Deployment:
- Deploy load balancers, DDoS protection, and redundant servers.
- Implement automatic backups and failover systems.
- Use high-availability (HA) architectures to minimize downtime.
2. DAD Model: Identifying and Mitigating Threats
The DAD model focuses on the three primary security risks that oppose the CIA triad.
⚠️ Disclosure (Threat to Confidentiality)
Unauthorized exposure of sensitive information.
✅ Mitigation:
- Apply data masking, encryption, and access controls.
- Implement security awareness training to prevent phishing attacks.
⚠️ Alteration (Threat to Integrity)
Unauthorized modifications to data or systems.
✅ Mitigation:
- Use digital signatures, checksums, and blockchain for verification.
- Deploy SIEM (Security Information and Event Management) to detect anomalies.
⚠️ Destruction (Threat to Availability)
Loss or deletion of critical data or service disruptions.
✅ Mitigation:
- Implement automated backups and disaster recovery solutions.
- Use redundancy, failover clusters, and cloud replication.
3. AAA Framework: Controlling Access and Monitoring Activity
The AAA model ensures that only the right people have access to the right resources, with a system in place to track their actions.
🔑 Authentication (Who you are)
Verifying the identity of users before granting access.
✅ Implementation:
- Use MFA, biometrics, and password policies.
- Implement Identity and Access Management (IAM) solutions.
🔑 Authorization (What you can do)
Granting or restricting access based on user roles.
✅ Implementation:
- Enforce RBAC (Role-Based Access Control) and attribute-based access control (ABAC).
- Implement least privilege principles to minimize access rights.
🔑 Accounting (What you did)
Tracking user activities for auditing and compliance.
✅ Implementation:
- Deploy SIEM for real-time monitoring and alerting.
- Maintain detailed logs of authentication and authorization events.
Bringing It All Together: Designing & Deploying a Security Solution
To build an effective security strategy, organizations should:
1️⃣ Use CIA to define protection goals (Confidentiality, Integrity, Availability).
2️⃣ Identify DAD threats and implement countermeasures.
3️⃣ Enforce AAA to secure access and track activities.
By integrating these models into security policies and solutions, organizations can enhance data protection, reduce risks, and improve compliance.
🚀 How does your organization apply these principles? Let’s discuss! #CyberSecurity #InfoSec #SecuritySolutions