Understanding and effectively responding to cybersecurity threats is crucial for businesses’ mission of enhancing cybersecurity awareness. Here’s how various risk response strategies can be applied to specific cybersecurity threats:
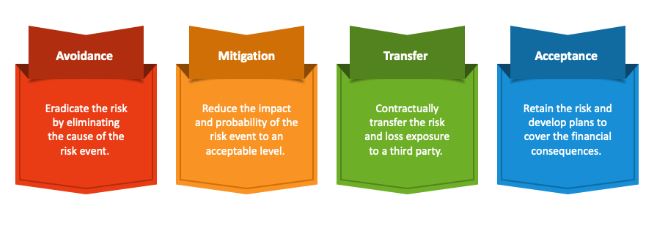
1. Avoidance (Eliminating the Risk)
- Threat: Using outdated software with known vulnerabilities.
- Response: Decommission unsupported software and transition to secure, updated platforms.
2. Mitigation (Reducing the Risk)
- Threat: Phishing attacks targeting employees.
- Response: Implement comprehensive training programs to educate staff on recognizing phishing attempts and establish robust email filtering systems.
- Threat: Ransomware incidents.
- Response: Maintain regular, secure backups and develop a detailed incident response plan to quickly address ransomware threats.
3. Transfer (Shifting the Risk)
- Threat: Financial repercussions from data breaches.
- Response: Purchase cyber insurance policies to offset potential financial losses associated with breaches.
4. Acceptance (Tolerating the Risk)
- Threat: Minor, non-critical system vulnerabilities.
- Response: Acknowledge the risk without immediate action, especially if mitigation costs outweigh potential impacts.
5. Deterrence (Discouraging Attackers)
- Threat: Unauthorized access attempts.
- Response: Enforce strict legal policies, monitor systems continuously, and communicate potential legal actions against unauthorized activities.
Implementing Risk Mapping
To effectively manage these threats, your business should develop a risk map. This visual tool helps in:
- Identifying Risks: Cataloging potential threats to the organization.
- Assessing Impact and Likelihood: Evaluating the severity and probability of each risk.
- Prioritizing Responses: Allocating resources to address the most significant threats first.
Risk mapping facilitates a clear understanding of the organization’s risk landscape, ensuring informed decision-making.