-
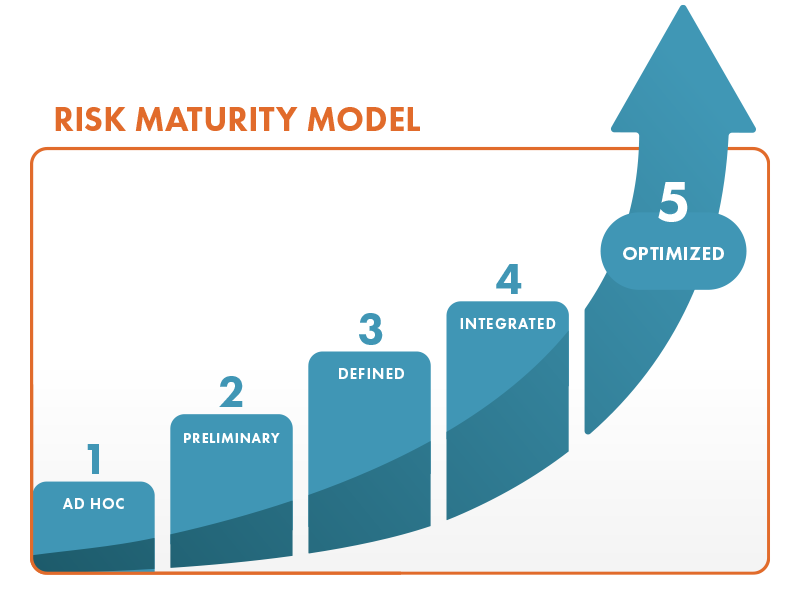
Is Your Risk Management Strategy Mature Enough?
Risk isn’t just something to react to—it’s something to manage proactively. That’s where RMM (Risk Maturity Model) comes in. It…
-

Compliance Checking (Testing)?
Compliance checking (or compliance testing) is the process of evaluating whether an organization, system, or process adheres to regulations, policies,…
-
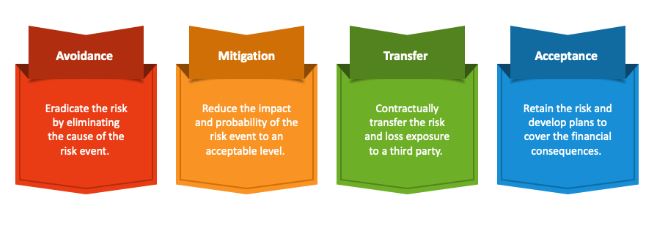
Risk Response Strategies in Cybersecurity
Understanding and effectively responding to cybersecurity threats is crucial for businesses’ mission of enhancing cybersecurity awareness. Here’s how various risk…
-

How cybersecurity policies works in employment process:
There are some concepts involved in this process: Job Descriptions, IAM, Onboarding & Least Privilege 🔹 Job Descriptions & Security…
-
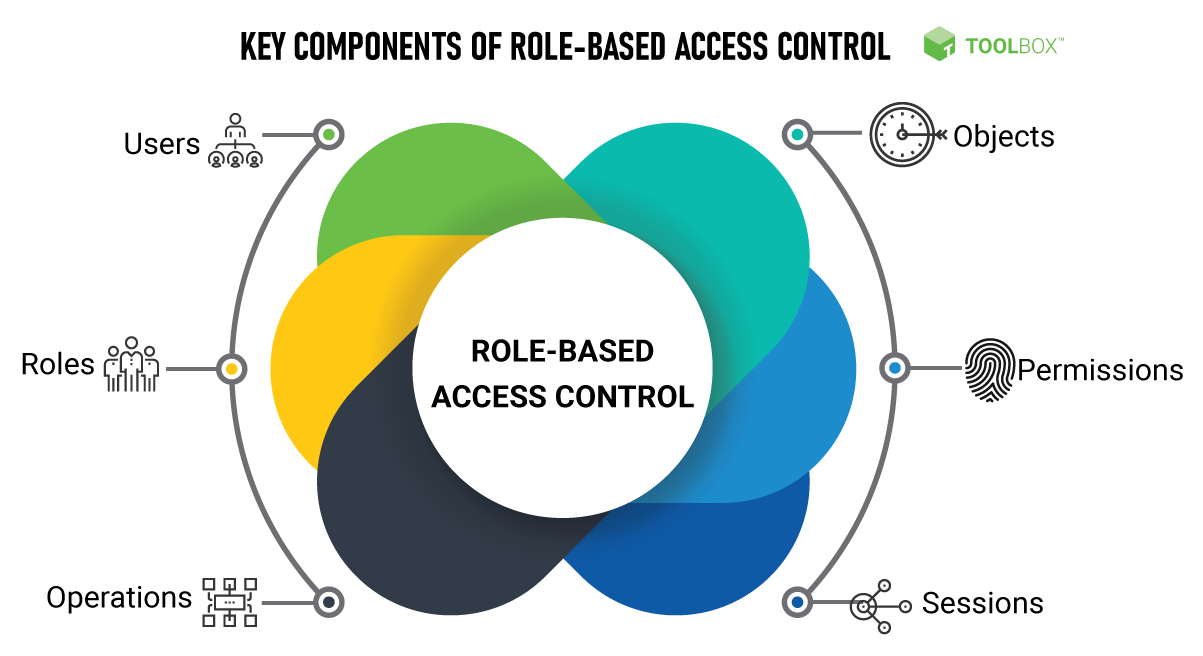
How Role-Based Access Control (RBAC) Improves Security Control
Role-Based Access Control (RBAC) enhances security by ensuring that users only have access to the resources necessary for their job…
-
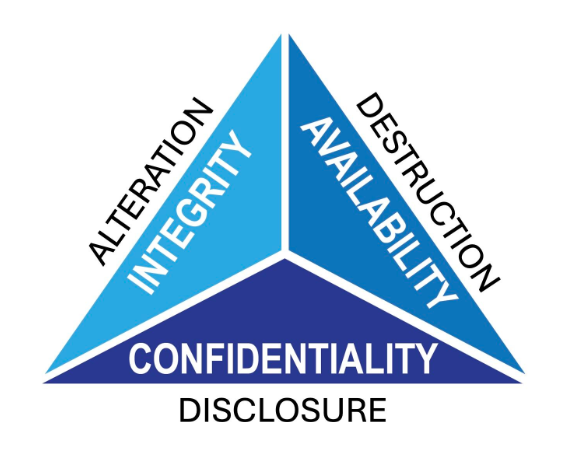
How CIA, DAD, and AAA Work in Designing a Security Policy & Deploying a Security Solution
A strong security policy and solution deployment require a structured approach to protect systems, data, and users. Three key security…
-

How CIA, DAD and AAA works in designing a security policy and deploying a security solution?
1. CIA Triad (Confidentiality, Integrity, Availability) The CIA triad ensures that security measures align with core protection goals. Designing a…
-

What is Cybersecurity Awareness
Cybersecurity awareness is the knowledge of how to protect against cyber threats and how to respond to them. It also includes understanding…

