-
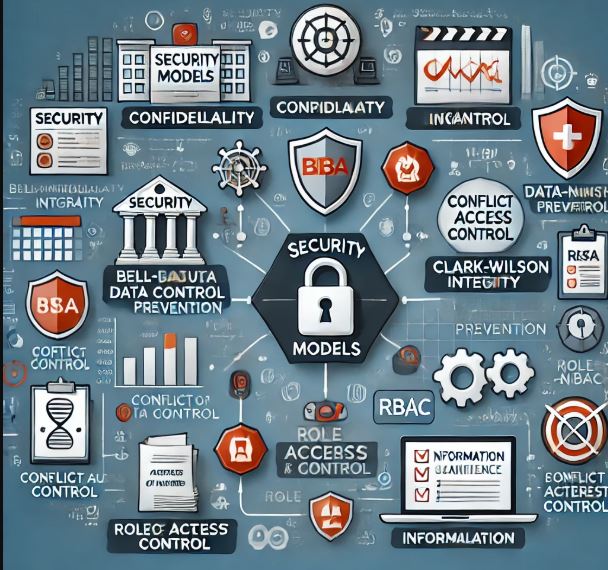
Security Models in Risk Management
Security models, with their formalized frameworks, play a critical role in risk management and auditing by providing structured ways to…
-

Encryption
1️⃣ Why is Encryption Important? ✅ Data Security: Protects sensitive information from hackers.✅ Privacy: Ensures only authorized users can access…
-

What is Data Hiding?
Data hiding is a cybersecurity and programming concept that restricts access to certain information to enhance security, privacy, and maintainability.…
-

What is Abstraction?
Abstraction is the concept of hiding complexity and showing only the essential details while suppressing the underlying implementation. It is…
-
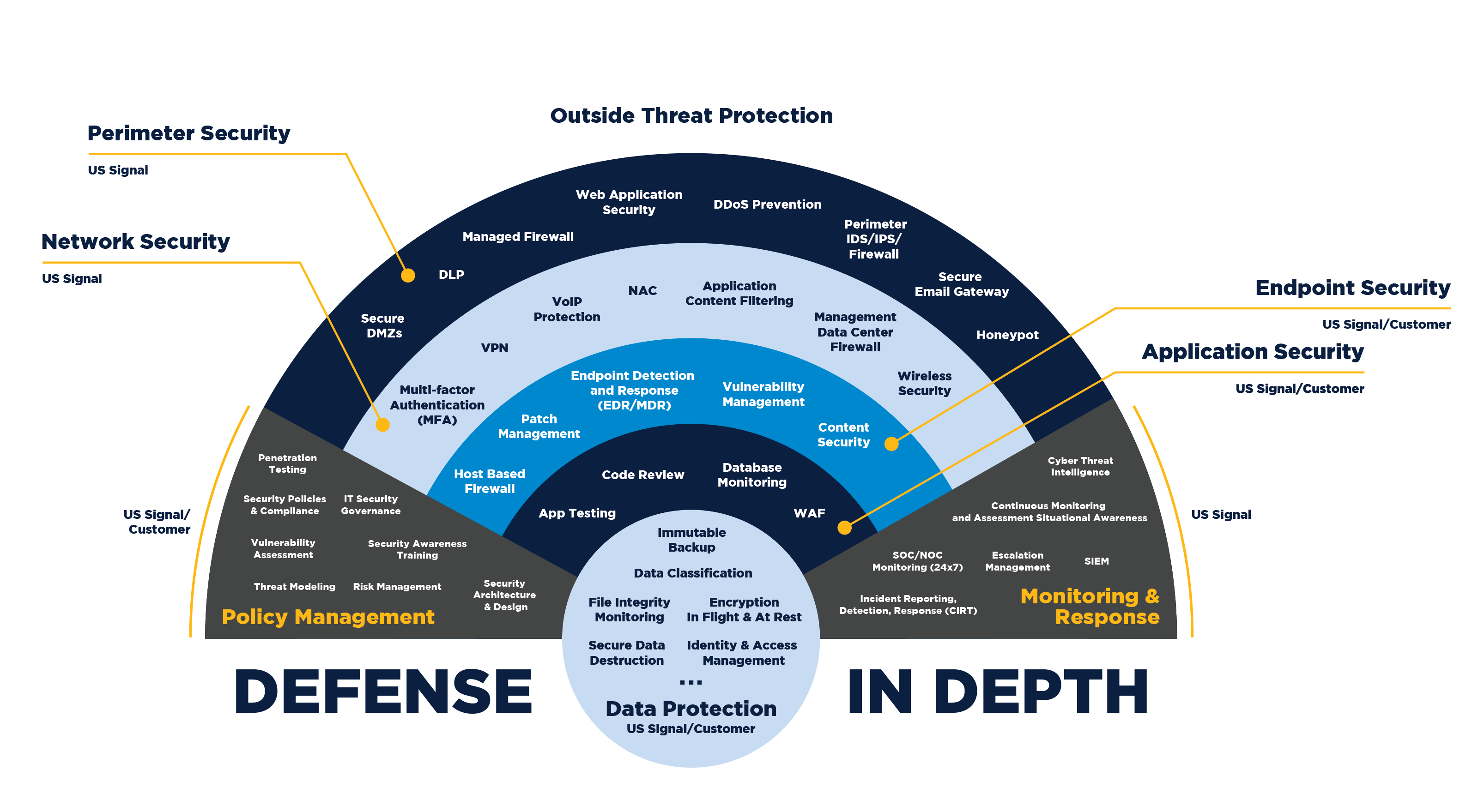
Defense in Depth (DiD)
A Multi-Layered Security Strategy Defense in Depth (DiD) is a cybersecurity strategy that implements multiple layers of security controls to…
-
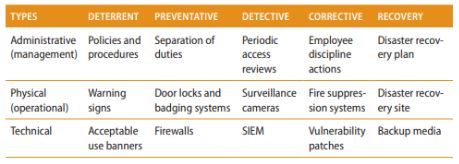
Types and Purpose of Security Controls
Security controls are measures designed to protect the confidentiality, integrity, and availability (CIA Triad) of systems and data. These controls…
-
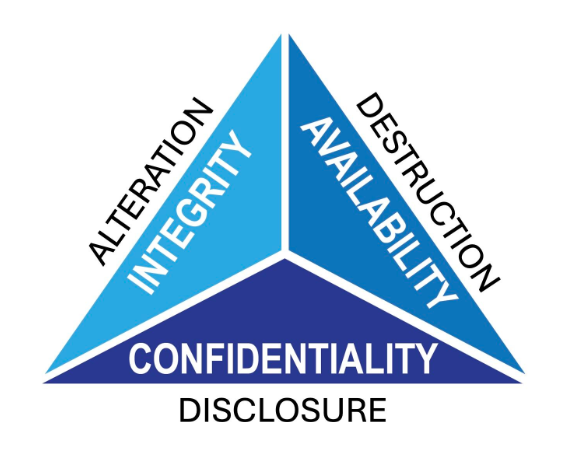
How CIA, DAD, and AAA Work in Designing a Security Policy & Deploying a Security Solution
A strong security policy and solution deployment require a structured approach to protect systems, data, and users. Three key security…
-

How CIA, DAD and AAA works in designing a security policy and deploying a security solution?
1. CIA Triad (Confidentiality, Integrity, Availability) The CIA triad ensures that security measures align with core protection goals. Designing a…

