-

Change Management & Security: Why It’s Critical for Cyber Resilience
Change management plays a crucial role in improving security by providing structured processes to manage, monitor, and mitigate risks associated…
-

𝗧𝗵𝗲 𝘁𝗼𝗽 𝗺𝗼𝘀𝘁 𝘂𝘀𝗲𝗳𝘂𝗹 𝗰𝘆𝗯𝗲𝗿𝘀𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗹𝗮𝘄𝘀:
𝟭. 𝗚𝗲𝗻𝗲𝗿𝗮𝗹 𝗗𝗮𝘁𝗮 𝗣𝗿𝗼𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗥𝗲𝗴𝘂𝗹𝗮𝘁𝗶𝗼𝗻 (𝗚𝗗𝗣𝗥) – 𝗘𝘂𝗿𝗼𝗽𝗲 📌 Why It’s Useful: One of the strongest data protection laws. Protects…
-

What is Threat Modeling?
Threat modeling is a proactive cybersecurity process used to identify, analyze, and mitigate potential threats before they can exploit system…
-

𝗛𝗼𝘄 𝗔𝗰𝗾𝘂𝗶𝘀𝗶𝘁𝗶𝗼𝗻𝘀, 𝗠𝗲𝗿𝗴𝗲r𝘀, 𝗮𝗻𝗱 𝗗𝗶𝘃𝗲𝘀𝘁𝗶𝘁𝘂𝗿𝗲𝘀 𝗜𝗻𝗰𝗿𝗲𝗮𝘀𝗲 𝗢𝗿𝗴𝗮𝗻𝗶𝘇𝗮𝘁𝗶𝗼𝗻𝗮𝗹 𝗥𝗶𝘀𝗸
Mergers, acquisitions, and divestitures can transform businesses, but they also introduce significant risks—from cybersecurity threats to operational disruptions. Here’s why…
-

What is COBIT?
COBIT (Control Objectives for Information and Related Technologies) is a framework for IT governance and management, designed to help organizations…
-

Business Impact Analysis (BIA) for a Financial Company
Let’s apply the Business Impact Analysis (BIA) process to a financial company while aligning it with CISSP principles. A financial…
-
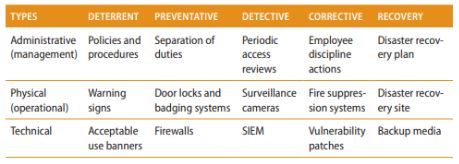
Types and Purpose of Security Controls
Security controls are measures designed to protect the confidentiality, integrity, and availability (CIA Triad) of systems and data. These controls…
-

Compliance Checking (Testing)?
Compliance checking (or compliance testing) is the process of evaluating whether an organization, system, or process adheres to regulations, policies,…
-
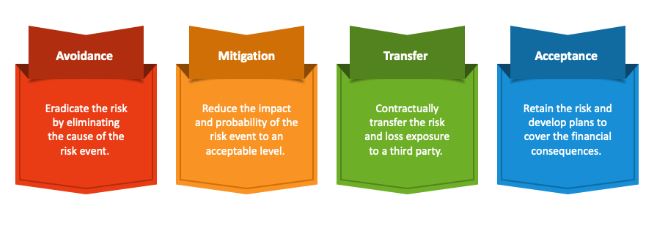
Risk Response Strategies in Cybersecurity
Understanding and effectively responding to cybersecurity threats is crucial for businesses’ mission of enhancing cybersecurity awareness. Here’s how various risk…
-
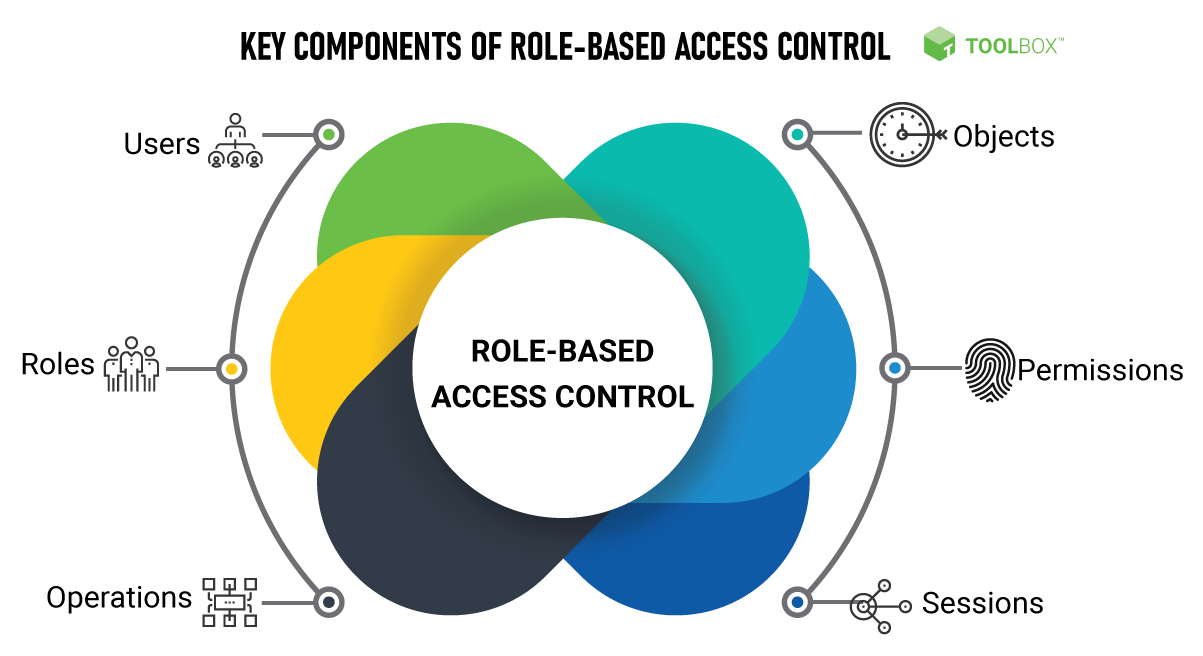
How Role-Based Access Control (RBAC) Improves Security Control
Role-Based Access Control (RBAC) enhances security by ensuring that users only have access to the resources necessary for their job…

