-

Change Management & Security: Why It’s Critical for Cyber Resilience
Change management plays a crucial role in improving security by providing structured processes to manage, monitor, and mitigate risks associated…
-

Memory Security Issues
Memory security issues refer to vulnerabilities, threats, and challenges related to the management and protection of memory in computer systems.…
-
🔹 𝗥𝗲𝗮𝗹-𝗪𝗼𝗿𝗹𝗱 𝗦𝗰𝗲𝗻𝗮𝗿𝗶𝗼𝘀 𝗼𝗳 𝗛𝗮𝘀𝗵𝗶𝗻𝗴 𝗔𝗹𝗴𝗼𝗿𝗶𝘁𝗵𝗺𝘀 𝗳𝗼𝗿 𝗜𝗻𝗱𝘂𝘀𝘁𝗿𝘆 𝗗𝗮𝘁𝗮 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆:
🔸 𝟭. 𝗦𝗲𝗰𝘂𝗿𝗲 𝗣𝗮𝘀𝘀𝘄𝗼𝗿𝗱 𝗦𝘁𝗼𝗿𝗮𝗴𝗲 (𝗕𝗮𝗻𝗸𝗶𝗻𝗴 & 𝗘𝗻𝘁𝗲𝗿𝗽𝗿𝗶𝘀𝗲𝘀) 📌 Scenario: A bank wants to store customer passwords securely to prevent…
-

𝗧𝗵𝗲 𝘁𝗼𝗽 𝗺𝗼𝘀𝘁 𝘂𝘀𝗲𝗳𝘂𝗹 𝗰𝘆𝗯𝗲𝗿𝘀𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗹𝗮𝘄𝘀:
𝟭. 𝗚𝗲𝗻𝗲𝗿𝗮𝗹 𝗗𝗮𝘁𝗮 𝗣𝗿𝗼𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗥𝗲𝗴𝘂𝗹𝗮𝘁𝗶𝗼𝗻 (𝗚𝗗𝗣𝗥) – 𝗘𝘂𝗿𝗼𝗽𝗲 📌 Why It’s Useful: One of the strongest data protection laws. Protects…
-

𝗖𝘆𝗯𝗲𝗿 𝗔𝗜 (𝗔𝗿𝘁𝗶𝗳𝗶𝗰𝗶𝗮𝗹 𝗜𝗻𝘁𝗲𝗹𝗹𝗶𝗴𝗲𝗻𝗰𝗲 𝗶𝗻 𝗖𝘆𝗯𝗲𝗿𝘀𝗲𝗰𝘂𝗿𝗶𝘁𝘆)
Cyber AI refers to the use of artificial intelligence and machine learning techniques to enhance cybersecurity operations. It helps detect,…
-

𝗛𝗼𝘄 𝗘𝗺𝗽𝗹𝗼𝘆𝗲𝗲 𝗢𝘃𝗲𝗿𝘀𝗶𝗴𝗵𝘁 𝗖𝗮𝗻 𝗜𝗺𝗽𝗿𝗼𝘃𝗲 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆?
Employees are both an organization’s greatest asset and its biggest security risk. Effective employee oversight ensures that security policies are…
-
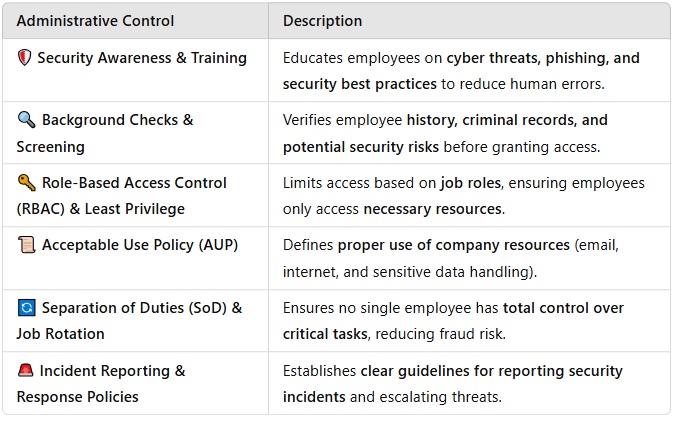
Six Administrative Controls to Secure Personnel
Administrative controls are policies, procedures, and practices designed to manage personnel security risks in cybersecurity. These controls ensure that employees…
-

How cybersecurity policies works in employment process:
There are some concepts involved in this process: Job Descriptions, IAM, Onboarding & Least Privilege 🔹 Job Descriptions & Security…
-

What is Cybersecurity Awareness
Cybersecurity awareness is the knowledge of how to protect against cyber threats and how to respond to them. It also includes understanding…

