-

Change Management & Security: Why It’s Critical for Cyber Resilience
Change management plays a crucial role in improving security by providing structured processes to manage, monitor, and mitigate risks associated…
-
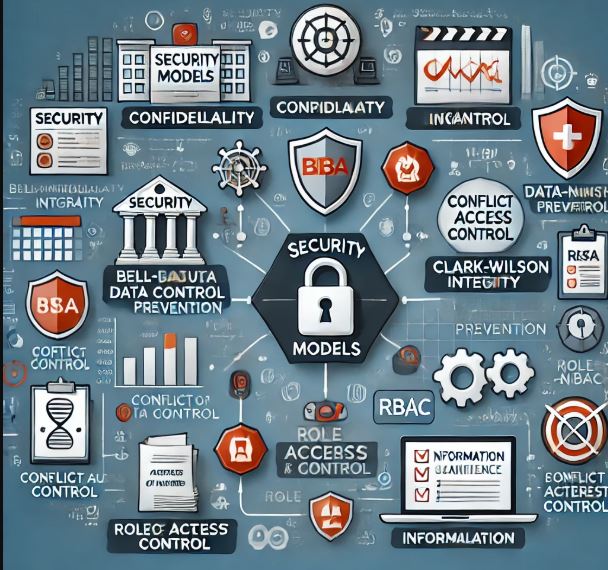
Security Models in Risk Management
Security models, with their formalized frameworks, play a critical role in risk management and auditing by providing structured ways to…
-

Keeping Team Morale High During Cybersecurity Incidents
In the high-stakes world of cybersecurity incidents, teams face intense pressure, long hours, and critical decision-making. Keeping morale high during…
-

𝗛𝗼𝘄 𝗘𝗺𝗽𝗹𝗼𝘆𝗲𝗲 𝗢𝘃𝗲𝗿𝘀𝗶𝗴𝗵𝘁 𝗖𝗮𝗻 𝗜𝗺𝗽𝗿𝗼𝘃𝗲 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆?
Employees are both an organization’s greatest asset and its biggest security risk. Effective employee oversight ensures that security policies are…
-

What is Threat Modeling?
Threat modeling is a proactive cybersecurity process used to identify, analyze, and mitigate potential threats before they can exploit system…
-

𝗛𝗼𝘄 𝗔𝗰𝗾𝘂𝗶𝘀𝗶𝘁𝗶𝗼𝗻𝘀, 𝗠𝗲𝗿𝗴𝗲r𝘀, 𝗮𝗻𝗱 𝗗𝗶𝘃𝗲𝘀𝘁𝗶𝘁𝘂𝗿𝗲𝘀 𝗜𝗻𝗰𝗿𝗲𝗮𝘀𝗲 𝗢𝗿𝗴𝗮𝗻𝗶𝘇𝗮𝘁𝗶𝗼𝗻𝗮𝗹 𝗥𝗶𝘀𝗸
Mergers, acquisitions, and divestitures can transform businesses, but they also introduce significant risks—from cybersecurity threats to operational disruptions. Here’s why…
-

What is COBIT?
COBIT (Control Objectives for Information and Related Technologies) is a framework for IT governance and management, designed to help organizations…
-

How the Delphi Technique Works in Cybersecurity
1️⃣ Expert Panel Selection – A group of cybersecurity experts is chosen based on their knowledge and experience in areas…
-
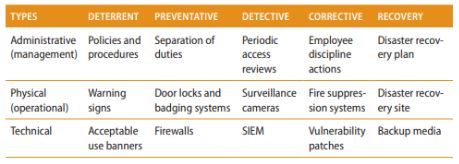
Types and Purpose of Security Controls
Security controls are measures designed to protect the confidentiality, integrity, and availability (CIA Triad) of systems and data. These controls…
-
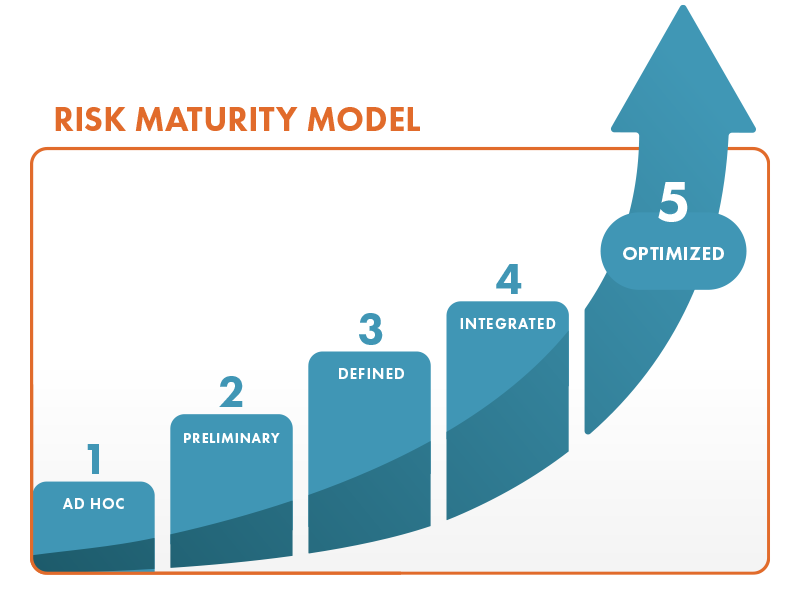
Is Your Risk Management Strategy Mature Enough?
Risk isn’t just something to react to—it’s something to manage proactively. That’s where RMM (Risk Maturity Model) comes in. It…

