-
🔹 𝗥𝗲𝗮𝗹-𝗪𝗼𝗿𝗹𝗱 𝗦𝗰𝗲𝗻𝗮𝗿𝗶𝗼𝘀 𝗼𝗳 𝗛𝗮𝘀𝗵𝗶𝗻𝗴 𝗔𝗹𝗴𝗼𝗿𝗶𝘁𝗵𝗺𝘀 𝗳𝗼𝗿 𝗜𝗻𝗱𝘂𝘀𝘁𝗿𝘆 𝗗𝗮𝘁𝗮 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆:
🔸 𝟭. 𝗦𝗲𝗰𝘂𝗿𝗲 𝗣𝗮𝘀𝘀𝘄𝗼𝗿𝗱 𝗦𝘁𝗼𝗿𝗮𝗴𝗲 (𝗕𝗮𝗻𝗸𝗶𝗻𝗴 & 𝗘𝗻𝘁𝗲𝗿𝗽𝗿𝗶𝘀𝗲𝘀) 📌 Scenario: A bank wants to store customer passwords securely to prevent…
-

𝗛𝗼𝘄 𝗔𝗰𝗾𝘂𝗶𝘀𝗶𝘁𝗶𝗼𝗻𝘀, 𝗠𝗲𝗿𝗴𝗲r𝘀, 𝗮𝗻𝗱 𝗗𝗶𝘃𝗲𝘀𝘁𝗶𝘁𝘂𝗿𝗲𝘀 𝗜𝗻𝗰𝗿𝗲𝗮𝘀𝗲 𝗢𝗿𝗴𝗮𝗻𝗶𝘇𝗮𝘁𝗶𝗼𝗻𝗮𝗹 𝗥𝗶𝘀𝗸
Mergers, acquisitions, and divestitures can transform businesses, but they also introduce significant risks—from cybersecurity threats to operational disruptions. Here’s why…
-

How the Delphi Technique Works in Cybersecurity
1️⃣ Expert Panel Selection – A group of cybersecurity experts is chosen based on their knowledge and experience in areas…
-
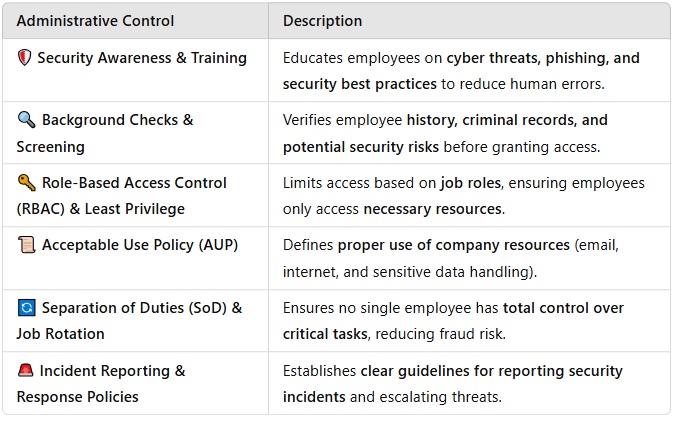
Six Administrative Controls to Secure Personnel
Administrative controls are policies, procedures, and practices designed to manage personnel security risks in cybersecurity. These controls ensure that employees…
-

How cybersecurity policies works in employment process:
There are some concepts involved in this process: Job Descriptions, IAM, Onboarding & Least Privilege 🔹 Job Descriptions & Security…

