-
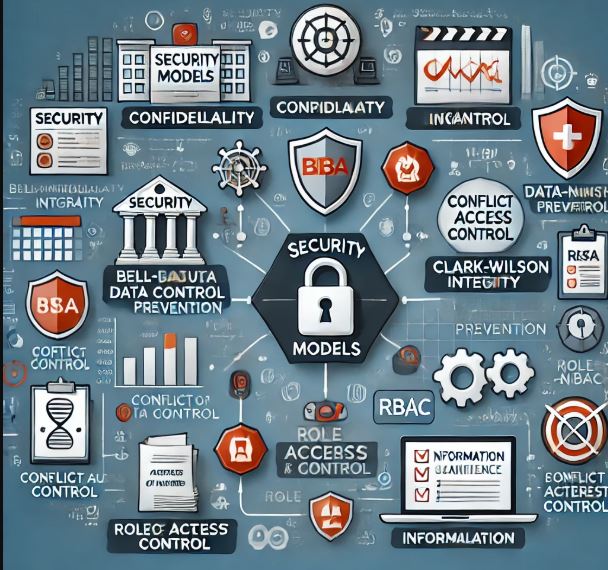
Security Models in Risk Management
Security models, with their formalized frameworks, play a critical role in risk management and auditing by providing structured ways to…
-

𝗛𝗼𝘄 𝗘𝗺𝗽𝗹𝗼𝘆𝗲𝗲 𝗢𝘃𝗲𝗿𝘀𝗶𝗴𝗵𝘁 𝗖𝗮𝗻 𝗜𝗺𝗽𝗿𝗼𝘃𝗲 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆?
Employees are both an organization’s greatest asset and its biggest security risk. Effective employee oversight ensures that security policies are…
-

What is Threat Modeling?
Threat modeling is a proactive cybersecurity process used to identify, analyze, and mitigate potential threats before they can exploit system…
-
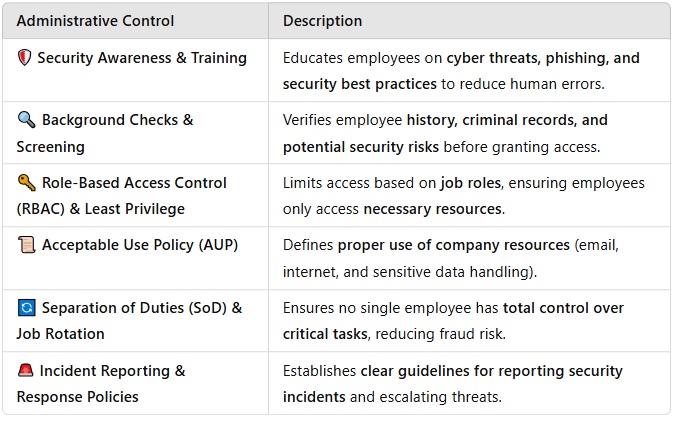
Six Administrative Controls to Secure Personnel
Administrative controls are policies, procedures, and practices designed to manage personnel security risks in cybersecurity. These controls ensure that employees…
-
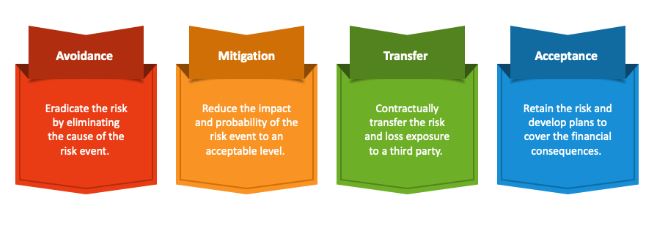
Risk Response Strategies in Cybersecurity
Understanding and effectively responding to cybersecurity threats is crucial for businesses’ mission of enhancing cybersecurity awareness. Here’s how various risk…
-

How cybersecurity policies works in employment process:
There are some concepts involved in this process: Job Descriptions, IAM, Onboarding & Least Privilege 🔹 Job Descriptions & Security…
-
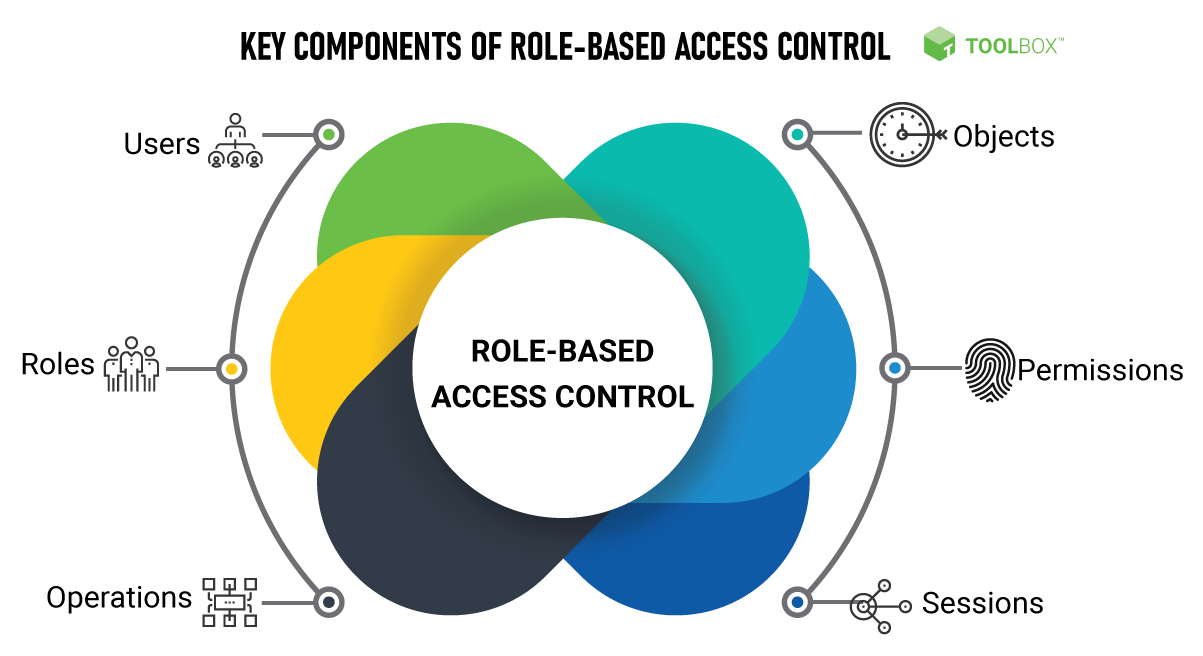
How Role-Based Access Control (RBAC) Improves Security Control
Role-Based Access Control (RBAC) enhances security by ensuring that users only have access to the resources necessary for their job…
-
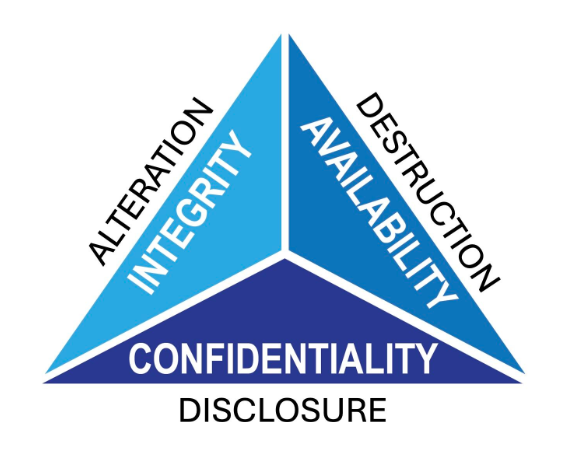
How CIA, DAD, and AAA Work in Designing a Security Policy & Deploying a Security Solution
A strong security policy and solution deployment require a structured approach to protect systems, data, and users. Three key security…
-

How CIA, DAD and AAA works in designing a security policy and deploying a security solution?
1. CIA Triad (Confidentiality, Integrity, Availability) The CIA triad ensures that security measures align with core protection goals. Designing a…

