-
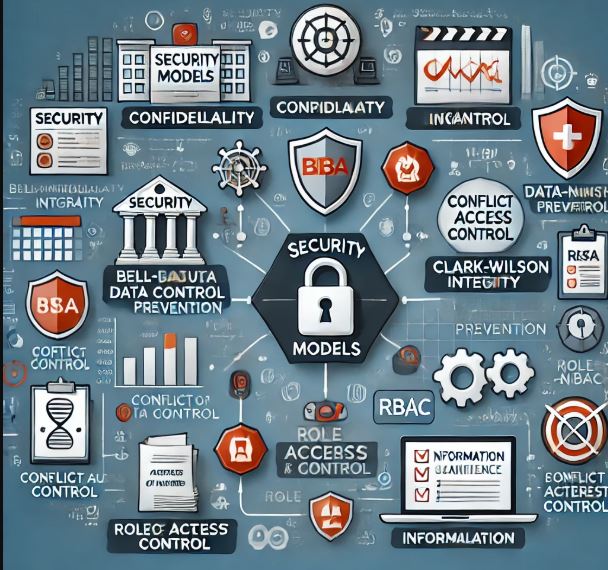
Security Models in Risk Management
Security models, with their formalized frameworks, play a critical role in risk management and auditing by providing structured ways to…
-

𝗛𝗼𝘄 𝗔𝗰𝗾𝘂𝗶𝘀𝗶𝘁𝗶𝗼𝗻𝘀, 𝗠𝗲𝗿𝗴𝗲r𝘀, 𝗮𝗻𝗱 𝗗𝗶𝘃𝗲𝘀𝘁𝗶𝘁𝘂𝗿𝗲𝘀 𝗜𝗻𝗰𝗿𝗲𝗮𝘀𝗲 𝗢𝗿𝗴𝗮𝗻𝗶𝘇𝗮𝘁𝗶𝗼𝗻𝗮𝗹 𝗥𝗶𝘀𝗸
Mergers, acquisitions, and divestitures can transform businesses, but they also introduce significant risks—from cybersecurity threats to operational disruptions. Here’s why…
-

Business Impact Analysis (BIA) for a Financial Company
Let’s apply the Business Impact Analysis (BIA) process to a financial company while aligning it with CISSP principles. A financial…
-
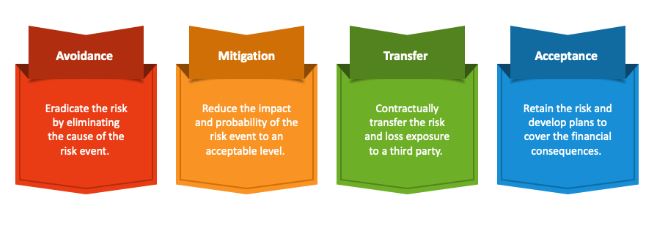
Risk Response Strategies in Cybersecurity
Understanding and effectively responding to cybersecurity threats is crucial for businesses’ mission of enhancing cybersecurity awareness. Here’s how various risk…
-

How cybersecurity policies works in employment process:
There are some concepts involved in this process: Job Descriptions, IAM, Onboarding & Least Privilege 🔹 Job Descriptions & Security…
-
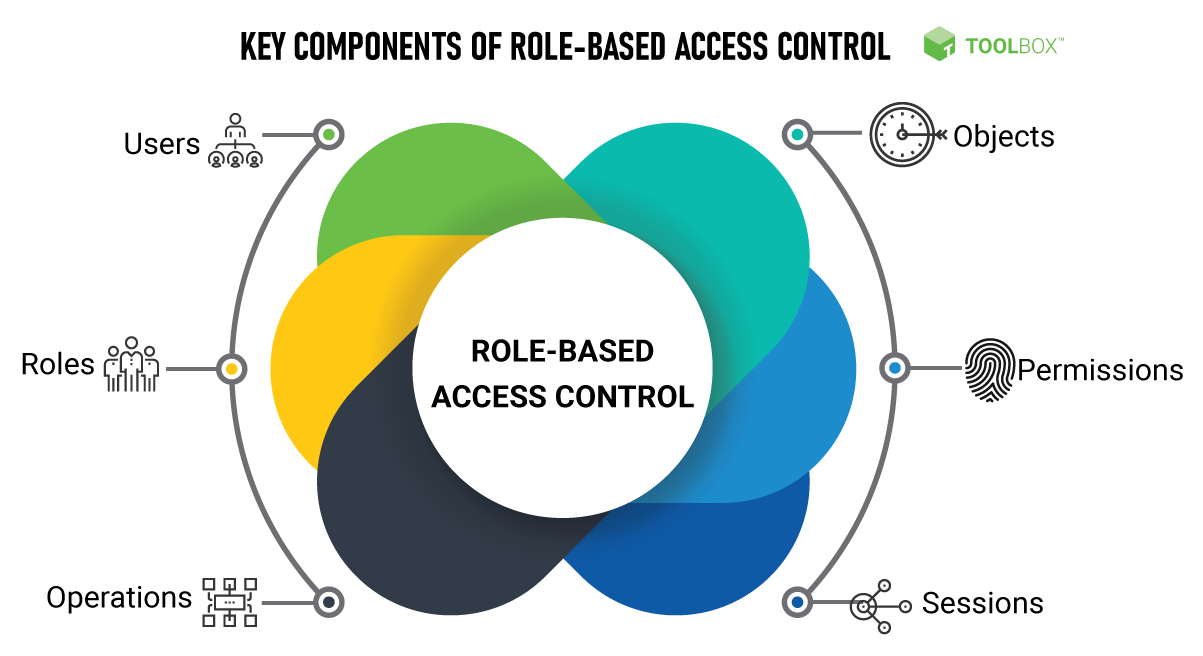
How Role-Based Access Control (RBAC) Improves Security Control
Role-Based Access Control (RBAC) enhances security by ensuring that users only have access to the resources necessary for their job…
-
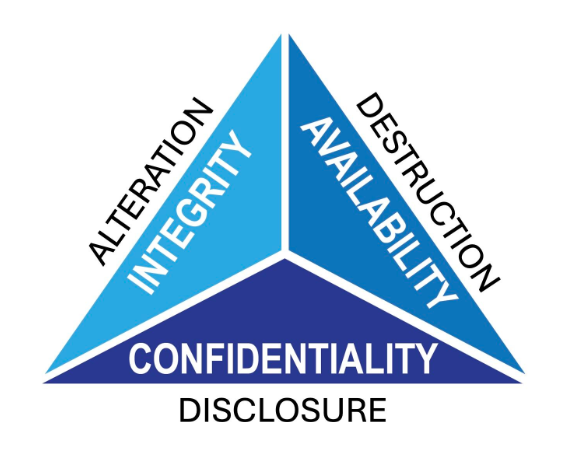
How CIA, DAD, and AAA Work in Designing a Security Policy & Deploying a Security Solution
A strong security policy and solution deployment require a structured approach to protect systems, data, and users. Three key security…
-

How CIA, DAD and AAA works in designing a security policy and deploying a security solution?
1. CIA Triad (Confidentiality, Integrity, Availability) The CIA triad ensures that security measures align with core protection goals. Designing a…

