A Multi-Layered Security Strategy
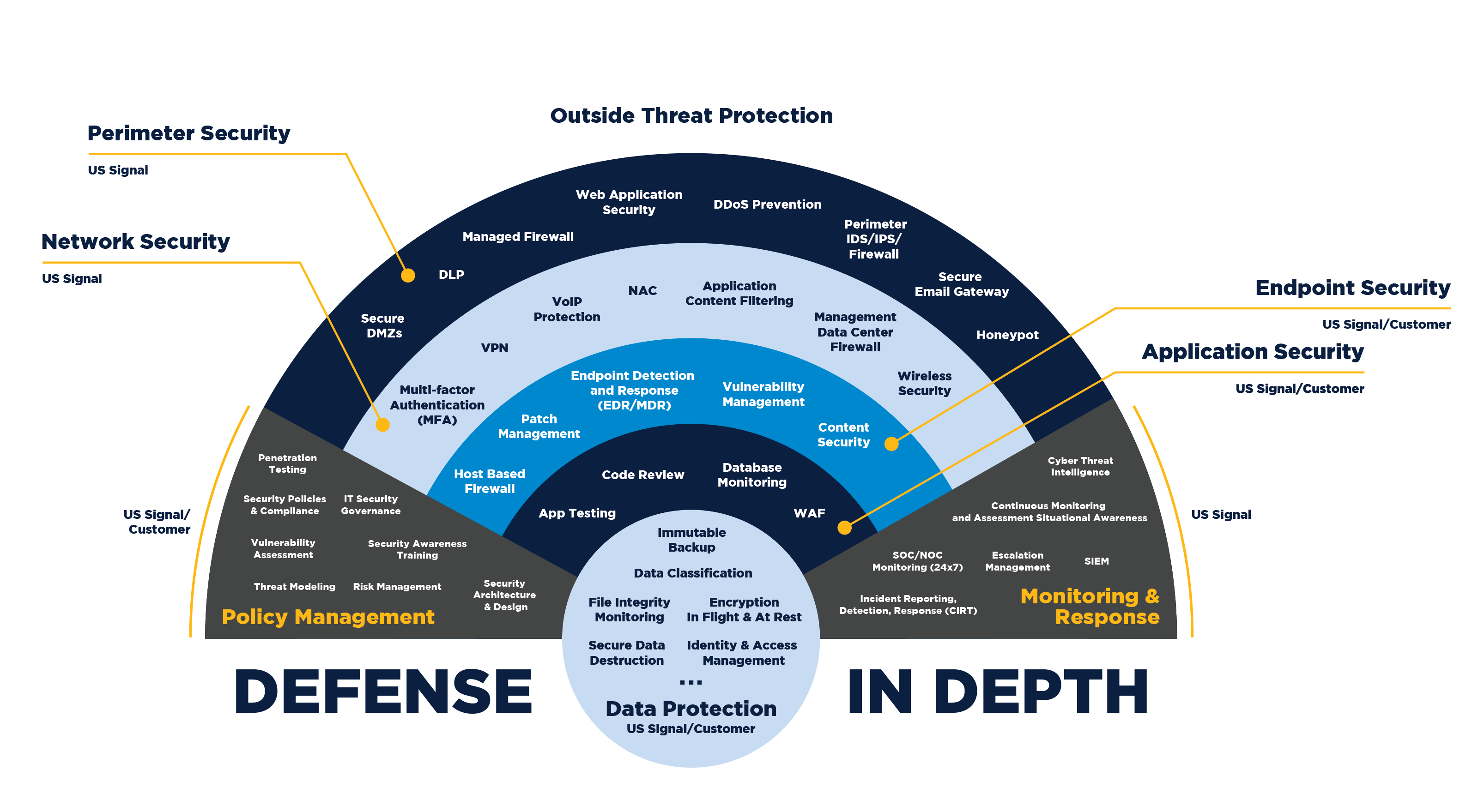
Defense in Depth (DiD) is a cybersecurity strategy that implements multiple layers of security controls to protect systems, data, and networks from cyber threats. The idea is that if one layer of defense is breached, additional layers continue to protect the system.
🔹 Key Principles of Defense in Depth:
Multiple Security Layers: Security mechanisms work together to reduce the risk of a single point of failure.
Redundancy: If one security measure fails, another layer provides protection.
Diverse Security Controls: Different types of controls (technical, administrative, and physical) are used to defend against various attack vectors.
Threat Detection and Response: Continuous monitoring and rapid incident response strengthen security.
🔹 Layers of Defense in Depth:
✅ Physical Security: Protects hardware (e.g., security cameras, biometric access, locked server rooms).
✅ Perimeter Security: Defends against external threats (e.g., firewalls, intrusion detection systems).
✅ Network Security: Ensures safe data transmission (e.g., VPNs, network segmentation).
✅ Endpoint Security: Protects individual devices (e.g., antivirus, endpoint detection and response).
✅ Application Security: Secures software and apps (e.g., web app firewalls, secure coding practices).
✅ Data Security: Protects sensitive information (e.g., encryption, data loss prevention).
✅ Identity & Access Management (IAM): Controls user access (e.g., multi-factor authentication, role-based access control).
✅ Security Awareness & Training: Educates employees to recognize and respond to threats (e.g., phishing simulations, cybersecurity training).
Real-World Example of Defense in Depth:
Imagine a company facing a ransomware attack:
🔹 A firewall blocks suspicious traffic.
🔹 If malware gets through, antivirus software detects and isolates it.
🔹 If a user mistakenly opens a phishing email, multi-factor authentication (MFA) prevents unauthorized access.
🔹 Data backups ensure quick recovery even if some files are encrypted.