-
Security Models in Risk Management
Security models, with their formalized frameworks, play a critical role in risk management and auditing by providing structured ways to…
-

𝗧𝗵𝗲 𝘁𝗼𝗽 𝗺𝗼𝘀𝘁 𝘂𝘀𝗲𝗳𝘂𝗹 𝗰𝘆𝗯𝗲𝗿𝘀𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗹𝗮𝘄𝘀:
𝟭. 𝗚𝗲𝗻𝗲𝗿𝗮𝗹 𝗗𝗮𝘁𝗮 𝗣𝗿𝗼𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗥𝗲𝗴𝘂𝗹𝗮𝘁𝗶𝗼𝗻 (𝗚𝗗𝗣𝗥) – 𝗘𝘂𝗿𝗼𝗽𝗲 📌 Why It’s Useful: One of the strongest data protection laws. Protects…
-

Keeping Team Morale High During Cybersecurity Incidents
In the high-stakes world of cybersecurity incidents, teams face intense pressure, long hours, and critical decision-making. Keeping morale high during…
-

What is Abstraction?
Abstraction is the concept of hiding complexity and showing only the essential details while suppressing the underlying implementation. It is…
-

Business Impact Analysis (BIA) for a Financial Company
Let’s apply the Business Impact Analysis (BIA) process to a financial company while aligning it with CISSP principles. A financial…
-
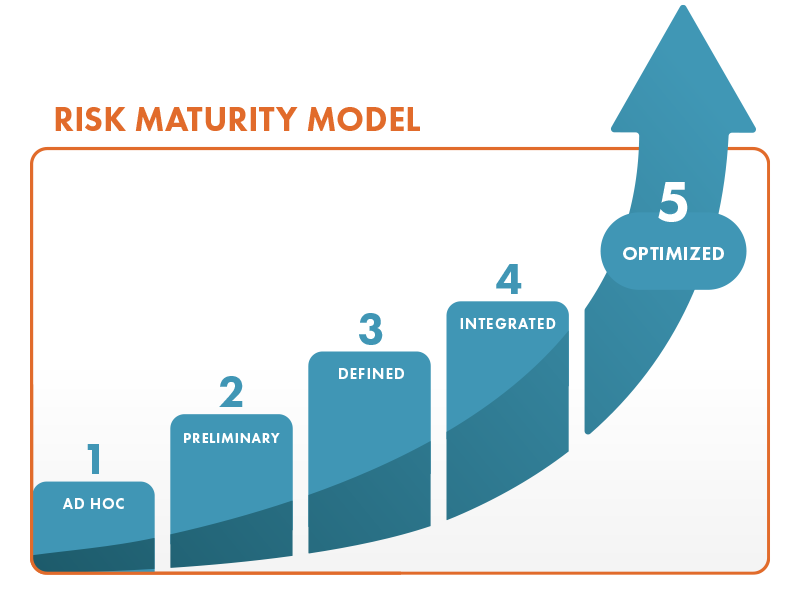
Is Your Risk Management Strategy Mature Enough?
Risk isn’t just something to react to—it’s something to manage proactively. That’s where RMM (Risk Maturity Model) comes in. It…

