Security controls are measures designed to protect the confidentiality, integrity, and availability (CIA Triad) of systems and data. These controls fall into three main categories: Administrative, Technical, and Physical controls, each serving different purposes such as Preventive, Detective, Corrective, Deterrent, and Compensating controls.
🔹 Types of Security Controls
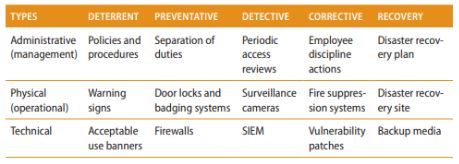
1️⃣ Administrative Controls – These include policies, procedures, and guidelines that define security rules and responsibilities. Examples: security training, access policies, background checks, and incident response plans.
2️⃣ Technical Controls (Logical Controls) – Implemented through software and hardware to protect systems from cyber threats. Examples: firewalls, encryption, multi-factor authentication (MFA), and intrusion detection systems (IDS).
3️⃣ Physical Controls – Designed to restrict unauthorized physical access to systems and facilities. Examples: security cameras, biometric locks, fences, and security guards.
🔸 Purpose of Security Controls
🔹 Preventive Controls – Aim to stop security incidents before they occur. Examples include firewalls, encryption, multi-factor authentication (MFA), and security awareness training.
🔹 Detective Controls – Help identify and monitor security incidents. Common examples are intrusion detection systems (IDS), security logs, and SIEM solutions.
🔹 Corrective Controls – Mitigate and respond to security breaches. This includes incident response plans, restoring backups, and applying patches.
🔹 Deterrent Controls – Discourage attackers from attempting an attack. Examples include warning banners, strict security policies, and legal penalties.
🔹 Compensating Controls – Provide an alternative when a primary security control is not feasible. For example, a Virtual Private Network (VPN) can be used when physical security is weak.
🚀 Why Are Security Controls Important?
✅ Reduce risks and vulnerabilities 🔐
✅ Ensure compliance with security standards (NIST, ISO 27001, GDPR, PCI-DSS) 📜
✅ Protect sensitive data from cyber threats 🔒
✅ Maintain business continuity and operational security 🏢
At SentraOne, we specialize in security awareness and risk management to help organizations strengthen their security posture. Want to enhance your cybersecurity strategy? Let’s connect! 🚀
#CyberSecurity #SecurityControls #RiskManagement #CISSP #DataProtection #SentraOne #Compliance